Main navigation
News
by Wilson Wong, S K Tsui, Alex Lam
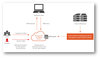
A Distributed Denial-of-Service (DDoS) attack is a cyber-attack, which an attacker tries to overload the targeted server/system with a huge volume of traffic from multiple, distributed sources (usually zombie computers), making the server/system unavailable to its intended users. As the attacks come ...
by S K Tsui
The majority of the wireless access points (APs) installed on campus were the outdated Aruba AP-125 model (product of year 2009) which supports legacy standards 802.11a/b/g/n but cannot support the 5th generation of Wi-Fi standard 802.11ac. In order to meet the increasing demands from user devices ...
by JUCC ISTF

/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Internet of Things (IoT) envisions everything in the physical world will be connected seamlessly and integrated securely through Internet infrastructure. When things react to ...
by Tony Chan
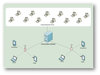
As a follow-up to our previous article on “A New look of Virtual Desktop Service for Students” (Ref: Network Computing Issue 89 - September 2016), several enhancements had been made on the VDS. In September 2016, 300 VDS concurrent connections were available for use by students and staff, and the ...
by Wilson Wong
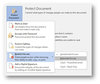
Security and user-friendliness tend to be in conflict with each other. From the security point of view, proper protection of sensitive information is critical. Sensitive data leakage not only damage the reputation of the University, it may also be harmful to the data custodians and related ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Wireless network (Wi-Fi) is now widely established and utilized at home, offices and everywhere in public areas such as rail stations, streets, and etc. This newsletter provides ...
by Joe Chow
As mentioned in the previous article (item 3 in Ref: Network Computing Issue 85 - September 2015), the first phase of desktop virtualization using Citrix Provisioning Service (PVS) had been implemented in selected teaching venues (a few lecture theatres, classrooms and CSC teaching studios) for ...
by Wilson Wong
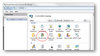
The CityU central web servers (www.cityu.edu.hk and www6.cityu.edu.hk) are load-balanced web farms, which provide high availability services to the communities. In case any server instance of a web farm is unavailable (due to errors or maintenance), other server instances of the same web farm can ...
by Joe Chow
The Policy Concept Windows policy, better known as Group Policy, is a feature of all Microsoft Windows operating systems (…Windows 7, Windows 8.1, Windows 10…) that controls the working environment and behaviour of a system. For example, a policy setting that allows or disallows remote access to ...
by JUCC ISTF

/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ According to a study conducted by IBM in 2012, it costs an organization US$80 per defect if vulnerabilities are identified early during the development stage, but the cost ...