Main navigation
News
by S K Tsui
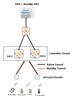
The CityU WLAN upgrade project began in 2017 ( Ref: Network Computing Issue 92 – June 2017 ) and has been ongoing for more than two years. During this period, the outdated Aruba Wi-Fi system was replaced to support the 5th generation of Wi-Fi standard 802.11ac (Wi-Fi 5). Up until now the Computing ...
by JUCC ISTF

/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Phishing refers to the malicious attack method by attackers who imitate legitimate companies in sending emails in order to entice people to share their passwords, credit card or ...
by Andes Cheung
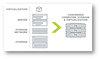
Introduction CityU currently maintains its own datacenters to provide an IT infrastructure supporting diverse services for teaching, research, administrative, and management use. Dated back a few decades ago, we have adopted a three-tier architecture consisting of compute, storage and networking ...
by JUCC ISTF

/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Authentication is the process of identifying the authenticity of a user. It can be accomplished by means of a combination of login ID (identification) and password (authentication ...
by Alex Lam
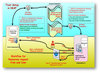
It is very common nowadays for students and staff to access research data, journals and courses online offered by other education institutions or companies over the Internet. The access usually requires users to sign up and create different user accounts. This article will detail how the Computing ...
by Cyril Ha
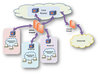
Background Information System Security has been a key concern over the past many years as more and more business processes rely on Information Technology to operate. Alike many other organizations, the usual first line of defense would be Internet protection with security devices such as a ...
by JUCC ISTF

/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ More and more transactions are performed online. Thus, a secured connection has to be ensured between the server and the client. However, connection mainly requires just a server ...
by S K Tsui

What is IoT? The Internet of Things (IoT) refers to billions of network devices, sensors and actuators around the world capable of gathering data (e.g. temperature, location, etc.) from the environment and sharing the data across the Internet. The data collected will then be analyzed, processed and ...
by Tony Chan
Since the first release of Windows 10 in July 2015, Microsoft has been providing feature updates for the operating system twice a year. Each version of Windows 10 was serviced with quality updates up to 18 months after its release. Users are strongly advised to upgrade their devices to the latest ...
by JUCC ISTF
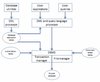
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ In universities, some data have to be shared with students, staff, guests whereas others have to remain protected. At the same time, the number of data leak and unauthorized ...