Main navigation
News
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Implementation of DLP solutions encompasses a variety of complex IT areas such as data classification, risk assessment, compilation of policies, standards and procedures. If not ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Data leakage refers to unauthorised transmission of data from within an organisation to an external destination or recipient. The transmission can be done both electronically and ...
by C Y Kwok

In order to cope with the ever increasing demands for Internet bandwidth of HARNET (Hong Kong Academic & Research Network) member institutions, especially in anticipation of new demands due to increased number of students arising from the 3-3-4 curriculum reform, a series of upgrades were carried ...
by Tony Chan

Newly released in January this year, Microsoft Office 2013 is the latest version of the Microsoft Office productivity suite designed to make creating, editing, reading and sharing documents easier and quicker. It is a cloud-based product that is closely integrated with SkyDrive, a free cloud storage ...
by Eric Shai

The CityUWiki was first introduced in June 2008. It is a document management and collaboration platform based on Microsoft SharePoint 2010. The usage of CityUWiki grew from 10 sites initially to over 100 sites as of today. It supports various departments, committees and project teams for closed ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Virtual machines are the containers in which guest operating systems and their applications run. In best practise, all virtual machines are isolated from one another. Virtual ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ The virtual networking layer consists of the virtual network devices through which virtual machines and the Service Console interface with the rest of the network. VM Server such ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ All configuration tasks for the VM Server are performed through the Service Console, including configuring storage, controlling aspects of virtual machine behaviour, and setting ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ A virtualisation infrastructure represents an additional architectural layer which can suffer from security vulnerabilities and be the target of attacks. Generally, attacks can be ...
by Manfred Chan
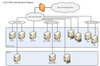
To exploit the cloud computing technologies, CityU has decided to adopt the Microsoft Office 365 (Office 365 hereafter) for Education. Office 365 is the cloud computing solution offered by the Microsoft for academic institutions. As an initial step, the Computing Services Centre (CSC) will replace ...