Main navigation
News
by JUCC ISTF

/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Cloud computing is a computing style in which scalable and flexible IT functionalities are delivered as a service to external customers using Internet technologies. Cloud ...
by Dick Wong
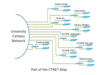
Due to a shortage of space, the university is exploring various ways to accommodate new staff and academic programmes. One way of tackling this problem is to adopt a “core-satellite” approach. The “core” represents premises in the Kowloon Tong main campus while “satellite” refers to remote offices ...
by Alex Lam

Overview Since the setup of student residence in year 2000, the number of users has grown from 800 to about 2800 this year. Furthermore, with the completion of phase 4 early next year, the number of residents will be further increased to around 3500. With the increase in the population and ...
by Wilson Wong
It is always recommended that a strong password should be used to resist guessing and brute-force attacks and lower the risk of security breach. An account with a weak password, such as a word in dictionary, can easily be broken by a hacker. He/She may then read, modify or delete all your files and ...
by Mei-ling Lee, Edward Chan
Today, we are living in a mobile world and our students are using their mobile devices to communicate electronically whenever and wherever they desire. To make use of the latest mobile technologies for their university learning and to take advantage of the high performance and reliable full campus ...
by Raymond Poon
Introduction Social media have become new ways we communicate with one another - both as an individual and as an institution. As an individual, by using social media tools such as Facebook, Twitter, YouTube, LinkedIn, Blogger, Flickr, etc., anyone with an Internet connection now has the ability to ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ The following security recommendations or guidelines help secure your server: 1. Rename the Administrator Account - Renaming the Administrator Account will help to prevent a brute ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ 1. Consider Using a Firewall For the network hosting the Terminal Server, it is best practice to use a firewall capable of stateful packet inspection. A firewall capable of ...
by JUCC ISTF
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */ Vulnerabilities in Remote Desktop Connection Vulnerabilities have been discovered in the Microsoft Remote Desktop Connection which could allow an attacker to take complete control ...
by Joe Lee
A. Printing a Single Copy of Course Work is Green According to the printing usage records in recent years, most students have printed one copy of their work only. Print Jobs 2009* 2010 * 20/1/2009 - 31/12/2009. Semester started on 12/1/2009. Printing system was upgraded on 20/1/2009 and able to ...